Protecting your employees, property, and company information requires an access control system for your business. All your questions about controlling access to your system are answered in today’s guide. Whether you want to know the definition, how it works, or the application, you will find everything here. Read on to learn more.
1. What is an access control system
An Access Control System ( ACS ) is a set of software and technical security tools, a set of usually automated procedures and/or processes that allow access to controlled areas or information to be controlled according to pre-established policies and rules. ACS can restrict and register the entry and exit of objects (people, vehicles) in a given area through access points (doors, gates, checkpoints).
The process of selectively restricting and managing the ability to enter or leave specific areas. The system relies on user credentials, access control readers, auditing, and reporting to track employee access in real-time to restricted business locations and exclusive areas such as data centers.
The main task of an access control system is to provide access control to a specific area: who is allowed to pass, when, and where, including identification of persons and/or vehicles. Additionally, access control systems help in solving working time recording tasks. Additionally, it can be integrated with accounting, personnel management, video surveillance, security, and fire alarm systems. An access control system plays an important role in a security compliance program because it keeps users’ information safe through restrictions and authorizations.
2. How the access control system works
Access control systems identify users by using PIN codes, smartphones, or biometrics. If the user is authenticated, the access control system authorizes the appropriate level of access and allows access to the user’s credentials and IP address. operate. Generally includes the following five steps:
1) Authorization
Authorization is the transformation of an unidentified individual into an authorized user. In this step, you can track who has access to the facility or specific areas. The company will use one of the access controls (RBAC, MAC, or DAC) to establish access policies to manage access rights. Each user’s role will specify which doors or areas can be accessed, and this information is then encoded into the credential. For places that frequently receive visitors or guests, it is important to design a system that grants such guests temporary access.
2) Authentication
During this step, you present your credentials (card, key card, smartphone, etc.) to the card reader. The access control system will then verify that you should be granted access by comparing it to a database of authorized users. Regardless of the outcome, the system stores data for each interaction for later reference when reviewing.
3) Visit
If the database thinks the credentials have the correct permissions, it will allow access to the area. This access is allowed by sending an output signal to an access control module (electronic door lock, electric lock, or magnetic lock) to release the door lock. In the case of a fail-safe lock, access is granted by suspending the lock’s electrical current and allowing it to be released. Failsafe locks, on the other hand, are released by applying an electrical current to the locking mechanism.
4) Management and monitoring
Administrative control of access to systems includes adding or removing credentials, changing permissions, adjusting schedules, or adding alerts. This process is handled by the system software backend. You can also monitor user and access point login logs. Modern access control software options offer cloud- or smartphone-based management.
5) Auditing and reporting
You can create logs of user activity, location activity, and access logs. Reporting is necessary to investigate suspicious activity and verify it during security threats. It also enables Chicago businesses to make informed decisions about their staffing and operating procedures, conduct standard security reviews, and maintain compliance standards.
The amount and type of detailed data provided by an access control system depends on the integration, such as visitor, time, attendance, and video systems. During an audit, it is important to determine how long the system stores data, whether accessing 1000 logs or unlimited log records. Once you understand your reporting requirements, you can create custom reports to save time.
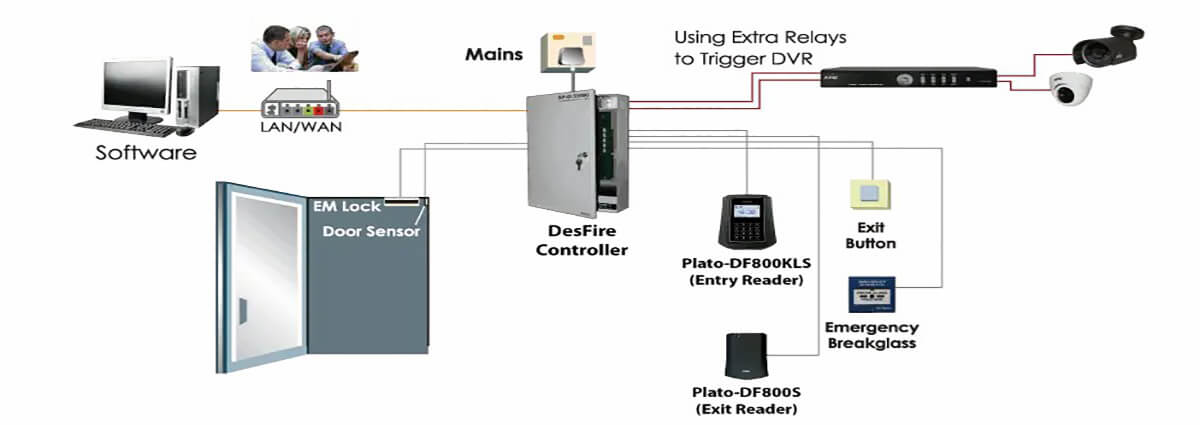
3. Basic components of an access control system
Access Control Systems There are various access control components, devices, and components, the following are some of the most commonly used components in access control systems.
1) Access control card
The access control card is what people call the key card. Each card has a unique code, and people use this code to unlock the door lock. The access control card is about the size of a credit card and can be carried in a wallet.
2) Card reader
A card reader is a device used to “read” credentials electronically. When a card reader is presented with a credential, it sends information about that credential to a control panel or network system hub to determine if access should be granted. If approved, the reader sends an output signal to release the door lock. Card readers are divided into the plug-in type and proximity type.
3) Keyboard
The keypad on the door lock is prepared for various opening methods of the door lock. When other unlocking methods cannot be used, you can also use the keypad to enter the correct password to unlock.
4) Access Control Panel
Access controllers are intelligent controllers for stand-alone systems. This panel allows permissions to be adjusted and access granted to all access control components in the building. Access control panels are located inside the building, but usually in private rooms.
5) Access control software
Access control software is the brains of the access control system, it manages the system and allows authentication, authorization, access, management, auditing, and reporting. The system can range from small establishments with just a few doors to multi-location businesses with thousands of doors. Additional features include remote management, monitoring security cameras, sending out bulk notifications, locking for emergencies, and more.
6) Physical Access Control Barriers
In addition to locked doors, there are many physical access control elements that can be used to prevent access to an area. Densely populated or vulnerable areas are often protected by physical barriers. Barriers to entry include turnstiles, high-speed doors, safety turnstiles, gate bars, and interlocks. Using non-traditional methods such as frosted glass and interior layout design, physical access can also be controlled and secured.
4. Advantages of access control systems
Businesses of all sizes prioritize security when it comes to protecting assets, confidential information, and employees. Among them, the access control system plays an indispensable role in the security of the enterprise. Let’s look at the advantages of access control systems.
1) Avoid the hassle of losing physical keys
The access control system is keyless entry, which means that you don’t have to carry a physical key with you every day, and it also saves you the hassle of losing your key. If a key card is lost, you can immediately delete it from the database and issue a new key card. If an employee leaves your company, his or her access can be removed in seconds. This convenience helps prevent unauthorized access through lost or duplicated keys and simplifies the process of granting or revoking access.
2) Protection against unwanted visitors
An access control system can reduce the likelihood of unwanted visitors entering your facility. Only authorized personnel with badges embedded in wireless technology or security codes can enter your business. With this system in place, you can ensure that everyone in the building is where they are supposed to be, enhancing overall security.
3) Prevent data leakage
Data is the new gold of modern society. Where there is personal data, there are people trying to buy it or steal it. Hackers can sell valuable data on the dark web black market, including social security numbers, credit card details, birthdays, and more. Therefore, businesses that handle private information, personal data, or sensitive details need to control who has direct access to this data and who has access to the computers or devices on which it is stored.
With the help of an access control system, information databases can be managed efficiently and effectively, thereby preventing data breaches from happening. Only those who are trusted with specific credentials can enter the database.
4) Real-time activity tracking
Another benefit of an access control system is that you can keep track of who comes in and out. With an access control system, you can know which employees move around your building and at what time. Additionally, in the event of a security incident, you’ll be able to see who swiped into a specific area at a specific time.
5) Easy to manage
Once you set up an access control system, you no longer need to worry about who needs what keys to get into which building, lab, or office. By providing remote access to control systems, you have full control over who can access restricted areas, minimizing security breaches and potential risks.
6) Protect personal safety
Access control systems let trusted people in and keep others out. Vandalism, robbery, and employee theft are all types of security risks that you can effectively prevent with an access control system. Another benefit is the ability to use an integrated access control system to address emergencies and incidents. Building access control systems can be designed with alarm or public address systems to help determine the fastest exit route during evacuation. Video surveillance helps to accurately and quickly identify the location of a fire or natural threat.
What’s more, the access control system is touchless, so there’s less chance of germs spreading between employees and visitors. This has become a key advantage of an access control system as the world grapples with a pandemic.
In today’s world, it is important to be prepared for the potential threat of individuals wanting to harm others and the risk that your facility may become an attack site. Security cameras can help prevent threats and escalations by accurately tracking specific people as they move within a building. Access control systems can further prevent movement throughout the building, confining intruders to non-life-threatening areas. Physical access control solutions are critical to the security of employees, equipment, infrastructure, and other company assets.
7) Improve the convenience of access
When you install an access control system, you don’t need to carry a heavy key ring every day. With an access control system, it’s easier to give everyone a programmed card, giving employees more flexibility in their schedules without requiring additional staff to grant access. Once you grant authorization, employees can access all the areas they need to do their jobs.
8) Versatility
Access control systems offer versatility in terms of applicable security hardware. For example, the system can be used for electric fences, turnstiles, gates, guardrails, parking lot doors, etc. It is convenient for you to realize one-key management through this system.
9) Improve business operations and efficiency
Developing a custom access control system is not only for safety and security, but also a tool to improve business operations, reduce unnecessary expenses, and increase efficiency. With the help of access control system reports, businesses can make better and more informed business decisions.
Tracking hourly and daily customer traffic helps businesses improve employee scheduling for greater efficiency.
- Businesses can find trends and patterns that affect customer service based on time, date, location, and specific employees.
- Employees can take more responsibility for attendance and tardiness by tracking employee behavior and when they come in and out
- Monitoring foot traffic data enables retail stores to create heat maps of in-store areas to better promote high-margin products.
- Business owners can remotely grant or arrange access to other individuals or companies without physically visiting the site.
5. Types of access control systems
There are four types of access control systems, and not all access control systems work the same. Therefore, you should choose the appropriate access control system according to your own needs.
1) Role-Based Access Control (RBAC)
The most common way to manage user permissions is through role-based access control (RBAC). In this method, permissions are granted to roles and then assigned to users. This approach includes permission-based access control, where permissions depend on attributes such as job, resource requirements, and environment. RBAC enables administrators to easily manage users in role-based groups. These groups can be segmented by title, location, authority, or whatever makes sense for your business.
In general, systems are designed to allow users to access only the information, areas, and schedules they need to do their jobs. As a result, users cannot access sensitive data that is not required to perform their duties. This is especially important when working with contractors, third-party organizations, large corporations, and the healthcare industry. Role-based security is a flexible and secure method of user rights management. For example, in a healthcare laboratory, all researchers have access to chemical storage rooms, but administrators cannot.
2) Rule-based access control
Rule-based access control is often used as an add-on to other types of access control. A rule-based access control system changes permissions based on rules created by an administrator, along with any type of access control you choose. For example, if your business closes at 5 pm, no one (not even managers) can enter your main office after closing.
3) Mandatory Access Control (MAC)
Mandatory access control systems provide the strictest protection, and the power to allow access falls entirely in the hands of the system administrator. This is the strictest access control. In this approach, the administrator must assign a label to each person. This label is based on an access control policy enforced uniformly for all users. Any action taken by the user will be tested against standardized policies to determine whether the action is allowed.
MAC is designed in hierarchical order. This makes it a common method for organizations that are increasingly concerned with secrecy and proper classification, such as military agencies. Users cannot override their own or other users’ access control policies. This helps ensure that access control policies are enforced consistently.
4) Autonomous Access Control (DAC)
Discretionary access control is the least restrictive permission management method. In this approach, administrators are responsible for deciding who can access a particular location. DAC allows individuals complete control over any areas they oversee and the associated devices in those areas. Discretionary access control provides more flexibility, but administrators can grant permissions to users who may not need them. This approach is often contrasted with the uniform application of permissions in mandatory access control.
6. Application of access control system
Access control systems are applicable to many industries, and any industry with security requirements can benefit from access control systems. For example:
- Healthcare: Hospitals Can Protect Patient Privacy With Access Control Systems
- Government: For working government jobs, confidentiality is paramount. The use of access control systems can limit hacker attacks and protect national information security.
- Enterprise: Access control systems can also restrict access to IT rooms and servers. They can keep track of who accessed certain data and when further protecting information.
- Education: Especially for universities with major research achievements, the access control system can prevent irrelevant people from entering the research site, or prevent boys from entering female dormitories. Make sure that only those with appropriate credentials have access to these areas.
- Worship Centers: Balancing safety and accessibility can be difficult in sanctuaries and spiritual centers that welcome all. With an access control system, worship centers can remain open during services and remain locked at other times.
- Hotel: Due to the large number of guests staying in the hotel, management is a difficult problem, and the access control system can help the hotel managers to achieve management more easily.
7. What are the access control plan considerations?
Consider the following factors before choosing an access control plan:
1) Technical security
- User Access: Define data sensitivity levels and assign appropriate user permission levels. User access is the use of spaces in the access control plan to set rules for passwords.
- Network Encryption and IT Security Protocols: The access control plan must include some methods of access control plan examples.
- Architecture: In an access control plan, how will you differentiate access control between levels and areas?
2) Physical security
- Network Identification and Control: What type of cabling is feasible in an access control plan?
- Perimeter security and cross-departmental requirements: Define access-restricted work areas and identify users with special authorizations for different departments.
- Physical Computer Control: Defines central control, monitoring, and reporting areas. Assign access rights to ground computer units and set up access control tools.
3) Administrative Security
- Role-Based Security and Oversight: Refers to the distribution of authority, national roles, and linkages of related duties and responsibilities within the access control program.
- Design a functional access control plan: guidance for employees at different risk levels, incident response and recovery steps, maintenance procedures, updating and reviewing the access control system in place.
8. Design a commercial access control system
If you’re new to security, choosing the business access control system that best suits your needs can be a big project for your business. There are hundreds of systems with a range of products and components, each with different integrations and capabilities. Open-source access control systems consist of various components from different manufacturers.
1) System planning and installation
Planning an electronic access control system is not easy. Here, a security consultant like iLockey can help make your decision easier. If you want to start this project yourself, there are a few things you should consider in your planning. That’s why iLockey has developed an in-depth access control system design guide to help you organize and plan the operational and technical tasks of installing an access control system. Fill out the quick contact form for instant access to a free downloadable PDF guide.
In this guide, you will learn:
- Access control system design
- Plan
- Buy
- Project management
- Test
- Train
- Participant
- Create operational levels
- Access right
- Set coupon
2) Manufacturer’s comments and suggestions
iLockey independently reviews many companies and products in the access control industry. As security consultants, it’s our job to separate “marketing hype” from what actually works. We provide an unbiased analysis of a product and its suitability for a particular application.
In these reviews, you can read our expert opinions on product manufacturers and their hardware and software. Our opinions will help you narrow your search for the best access control systems for your facility. If you want to customize your system with hardware and software from different manufacturers, you can also explore open-source access control options.
3) Configuration and model
As you begin planning your model and system configuration, it is important to identify factors that may affect functionality. It may be helpful to note which features are necessary and which are best. An effective enterprise access control system is the front line of protecting Illinois businesses. Cutting corners isn’t a good thing when you don’t know what’s coming. You need to make sure you have a clear understanding of the following things discussed in this article:
- Networked or standalone
- Door
- Number of access points
- External export
- Authority management
- Way credential type
- Hosting
- System installation method
- Third-party or internal monitoring
- Additional functions (such as anti-echo, biometric scanning, face recognition, video surveillance, and alarm)
9. Access control technology in 2023
It’s a very exciting time for access control technology. If you are looking to upgrade or install a new access control system this year, it is important that your solution is scalable and compatible with future technologies. Access control components and components have come a long way. Today’s systems integrate new capabilities to create complete business security solutions. With more and more data at our fingertips, we need to adjust our position and make real-time decisions to prevent problems before they happen.
1) Industry Status
We need to understand what we are protecting in the security industry. We need a solid understanding of access control technologies to create a seamless user experience, increase efficiency, and maximize the security of the work environment. We need to recognize the threats and risks posed by cyberattacks, hacking, social engineering, phishing, lost or stolen credentials, forced entry, and even simple user error. No access control system is 100% indestructible. However, you can eliminate many risks by having the right security and access control systems in place.
Technology has changed our daily lives. As more and more devices become smart and the Internet of Things grows, it is important to connect all the parts to form a complete system. Many operators have begun to re-evaluate how to use parts of their existing systems to leverage other parts of their operations to increase efficiency.
Using your phone for access and security is going mainstream. The younger generation is eager to try. Our smartphones rarely leave us. Now they use face recognition to unlock. Various security applications are constantly increasing: using mobile credentials to unlock electronic door locks, digital student ID cards, paying with smartphones, multi-factor authentication, time and attendance, and more.
2) Planning for the future
Future access control systems will see an increase in biometric scanning and facial recognition technology. Biometric solutions read a person’s physical characteristics to verify identity, rather than using standard credentials. Face recognition goes a step further. Faces are detected from different angles using artificial intelligence and machine learning. The system then matches faces to identities to ensure the person belongs to a specific area.
Besides these trends in access control technology, it is important to recognize the needs of emerging markets as well. The rapidly evolving cannabis industry presents a new set of challenges and opportunities for security and access control compliance.
10. Frequently asked questions about access control systems
The following are frequently asked questions about access control systems.
1) Why is an access control system so important?
According to research studies, having a proper access control system has become critical as cyber-attacks cost businesses millions of dollars every year.
A report by Interpol found that the costs associated with insider threat breaches in 2020 averaged $7.68 million. Unfortunately, that number continues to rise, and as more people work from home, companies experience a spike in security breaches.
Access control systems control who can view or use any given resource. This can translate into who can access and edit specific files, what types of devices can be used, or who can access specific devices in IT security settings.
2) How can my business implement a real-time access control system?
If you want to improve overall IT security and reduce risk, you should have an access control system. You can obtain relevant information by contacting iLockey, and by analyzing your business information, we will sincerely answer your questions at any time.
3) Why use an access control system instead of keys?
If someone loses a key, you need to replace the lock to ensure that the lost key cannot be misused. And you can’t see if and when someone used the key, so you don’t know who got in or when. Also, if you own a lot of buildings, you need a lot of keys, which are not convenient to carry and use.
11. Conclusion
Using an access control system can make your life easier, save you money, and keep your workplace safe. After reading this guide, I hope it will help you learn more about access control systems and understand how to choose an access control system. If you have any other questions, please feel free to contact iLockey.














Leave A Comment